Gnu Privacy Guard (GPG) is an open source PGP clone. It uses strong encryption to protect emails as well as files and folders. For encrypting drives, folders, and files I use a different piece of software (Truecrypt). GPG is my encryption tool for email. Continue reading
Gnu Privacy Guard (GPG) is an open source PGP clone. It uses strong encryption to protect emails as well as files and folders. For encrypting drives, folders, and files I use a different piece of software (Truecrypt). GPG is my encryption tool for email. Continue reading
Category Archives: Computing
Color blindness and accessibility
 In an effort to meet accessibility requirements, I was looking for tools to check whether users with a variety of color blindness conditions can actually use our websites. Posters and brochures can already be difficult to read for color blind people. On web sites another dimension is added to this problem because certain features may be rendered useless by choosing a bad color palette. Colored links for example, if not underlined, may not be seen as links because they appear to be of the same color as all other text. Continue reading
In an effort to meet accessibility requirements, I was looking for tools to check whether users with a variety of color blindness conditions can actually use our websites. Posters and brochures can already be difficult to read for color blind people. On web sites another dimension is added to this problem because certain features may be rendered useless by choosing a bad color palette. Colored links for example, if not underlined, may not be seen as links because they appear to be of the same color as all other text. Continue reading
Email Address Validation Tool
A regular expression for validating secure passwords
 For one of our current projects I was looking for a way to validate strong passwords with regular expressions. Form field validation requirements are defined as a regex in the database properties for the field, so the easiest way to set up secure passwords was using this method. I found many examples for regular expressions but they all lacked one important feature. Continue reading
For one of our current projects I was looking for a way to validate strong passwords with regular expressions. Form field validation requirements are defined as a regex in the database properties for the field, so the easiest way to set up secure passwords was using this method. I found many examples for regular expressions but they all lacked one important feature. Continue reading
XP Service Pack 3
![]() MS finally released Win XP SP3. Windows Update didn’t work, probably too many downlaods are attempted from this server. Download SP3 at Microsoft’s Download Center and install manually.
MS finally released Win XP SP3. Windows Update didn’t work, probably too many downlaods are attempted from this server. Download SP3 at Microsoft’s Download Center and install manually.
Free encryption software (3)
Hard disc encryption
 [Update Nov. 11, 2014: The Truecrypt developers no longer support this product]
[Update Nov. 11, 2014: The Truecrypt developers no longer support this product]
Since version 5, released on February 8, 2008, Truecrypt can encrypt an entire drive or partition, including the one that contains the operating system installation. Truecrypt’s implementation of strong drive encryption is particularly impressive. Listen to Security Now episode 133 for more information. Finally high quality free open source software is available for encrypting an entire hard disk. I immediately encrypted my Laptop’s hard disk. Continue reading
Free encryption software (2)
File encryption on USB flash drives
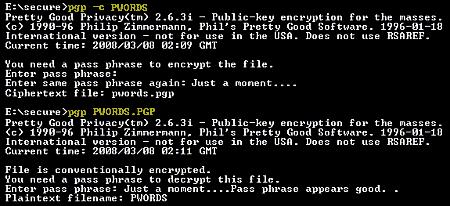
 I am a PGP user since 1996 and I still use Ståle Schumacher’s international DOS version 2.63i to encrypt files on my USB flash drives. All I need is PGP’s small exectutable file (pgp.exe, 237.737 kb). On first use, PGP will create a second small file that contains some random seed data for the encryption. With this minimal setup, PGP will warn you about a missing configuration file, but this does not affect the strength of encryption. The USB drive on my key ring contains an encrypted passwords file and pgp.exe, providing easy access to the many cryptic passwords I use. All I need is one strong master pass phrase to decrypt the file and get instant access to more passwords than I could ever remember.
I am a PGP user since 1996 and I still use Ståle Schumacher’s international DOS version 2.63i to encrypt files on my USB flash drives. All I need is PGP’s small exectutable file (pgp.exe, 237.737 kb). On first use, PGP will create a second small file that contains some random seed data for the encryption. With this minimal setup, PGP will warn you about a missing configuration file, but this does not affect the strength of encryption. The USB drive on my key ring contains an encrypted passwords file and pgp.exe, providing easy access to the many cryptic passwords I use. All I need is one strong master pass phrase to decrypt the file and get instant access to more passwords than I could ever remember.
I insert the USB drive and open a command prompt window (Start > Run > cmd).
PGP file encryption:
pgp -c filename
PGP file decryption:
pgp filename.pgp
In conventional -c encryption mode PGP uses a symmetric block encryption algorithm (IDEA) with a key size of 128 bits. Together with a good pass phrase this is really strong encryption.
Don’t forget to securely delete the plaintext file afterwards:
pgp -w filename
Since this version of PGP was developed for DOS, it only supports 8 character file names (8.3).
PGP 2.63i is still available from Ståle’s pgpi.org site [download].
Back in 1996 I contributed the “self-sign FAQ” to the PGP community.
Other Flash drive encrytion options for Windows, Mac and Linux
Many different free and commercial PGP versions and clones are available. See pgp.com, pgpi.org, and gnupg.org. I still use PGP 2.63i because it is an easy-to-use lightweight program that provides strong encryption and can be put on any device by simply copying one small file.
Truecrypt in “Traveller Mode” can be used to create an encrypted file container on Flash memory. Truecrypt is free and provides super strong encryption, too. However, you need to have administrator privileges on all machines that you decrypt the container on. I’m not an admin on my machine at work but need access to the passwords on my keyring there, too.
Some USB drives (SanDisk, Kingston, IronKey) have hardware encryption built in, but when it comes to encryption, I prefer to stay away from proprietary implementations.
Free encryption software (1): Introduction
Free encryption software (3): Hard disc encryption
Free encryption software (4): GNU Privacy Guard
Free encryption software (1)
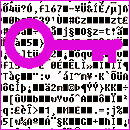 All data on my laptop’s hard drive is encrypted. If the machine gets stolen, no one will be able to boot the operating system without entering the correct pass phrase beforehand. Nothing on the drive looks like a file of has any readable information. My letters, photos, and all other private information are no more than an cryptic stream of random bytes. Continue reading
All data on my laptop’s hard drive is encrypted. If the machine gets stolen, no one will be able to boot the operating system without entering the correct pass phrase beforehand. Nothing on the drive looks like a file of has any readable information. My letters, photos, and all other private information are no more than an cryptic stream of random bytes. Continue reading
My first Laptop
You’ve probably met some wise computer veterans who constantly tell you that they started computing decades ago. And usually they talk about their first Atari or Commmodore 64, and how they wrote cool Assembler code to get it to do what they wanted it to do. I can’t impress anyone with my first 80286 desktop PC, but take a look at my first Laptop… Continue reading